Voice over Internet Protocol (VoIP)
has revolutionized how we communicate, offering cost-effective alternatives to traditional telephony. However, many users remain unaware of the underlying technology that powers these communications – the Session Initiation Protocol (SIP). As businesses and individuals increasingly adopt VoIP solutions, understanding SIP becomes crucial for IT professionals, developers, and even end-users.This article provides a comprehensive exploration of the SIP protocol, delving into its call flow mechanisms, message structures, and stack architecture. Whether you're a telecommunications professional looking to deepen your knowledge or a curious tech enthusiast, this guide will equip you with valuable insights into one of the internet's most important communication protocols.
What is the SIP Protocol?
SIP Definition and Purpose
The
Session Initiation Protocol (SIP)
is an application-layer signaling protocol designed to create, modify, and terminate multimedia sessions with one or more participants. Developed by the Internet Engineering Task Force (IETF), SIP has become the standard protocol for internet telephony, instant messaging, and video conferencing.Unlike protocols that handle data transmission, SIP focuses specifically on session management. It acts as a digital switchboard operator, establishing connections between users but leaving the actual media transmission to other protocols. This specialization allows SIP to remain lightweight while providing powerful session control capabilities.
SIP vs. VoIP vs. IP: Clearing the Confusion
There's often confusion surrounding the terms SIP, VoIP, and IP. Let's clarify:
- SIP (Session Initiation Protocol) is a specific communication protocol that manages multimedia sessions.
- VoIP (Voice over Internet Protocol) is a technology category that enables voice communications over IP networks. SIP is one of several protocols that can be used to implement VoIP.
- IP (Internet Protocol) is the fundamental network protocol that routes packets across interconnected networks.
Think of it this way: IP provides the roads, VoIP is the concept of driving, and SIP is a specific set of driving rules for a particular type of journey.
SIP's Place in the OSI Model
SIP operates at the application layer (Layer 7) of the OSI model. At this highest layer, SIP interfaces directly with applications and end-users, handling the semantics of the communication. By functioning at the application layer, SIP can work independently of the underlying transport protocols, offering flexibility in implementation.
Understanding SIP Call Flow
Basic SIP Call Flow: A Step-by-Step Explanation
The SIP call flow follows a logical sequence, somewhat similar to traditional telephony but with distinct digital characteristics. Let's examine a basic call flow between two users, Alice and Bob:
- INVITE: Alice sends an INVITE request to Bob, indicating she wants to establish a session.
- 100 Trying: The server acknowledges receipt of the INVITE and begins processing it.
- 180 Ringing: Bob's phone starts ringing, and a 180 Ringing response is sent back.
- 200 OK: Bob answers the call, and his device sends a 200 OK response.
- ACK: Alice's device acknowledges receipt of the 200 OK with an ACK message.
- Media Exchange: Direct media exchange begins between Alice and Bob.
- BYE: When either party wants to end the call, they send a BYE request.
- 200 OK: The other party acknowledges the call termination with a 200 OK response.
This flow may include additional steps depending on network complexity, presence of intermediaries, or specific feature requirements.
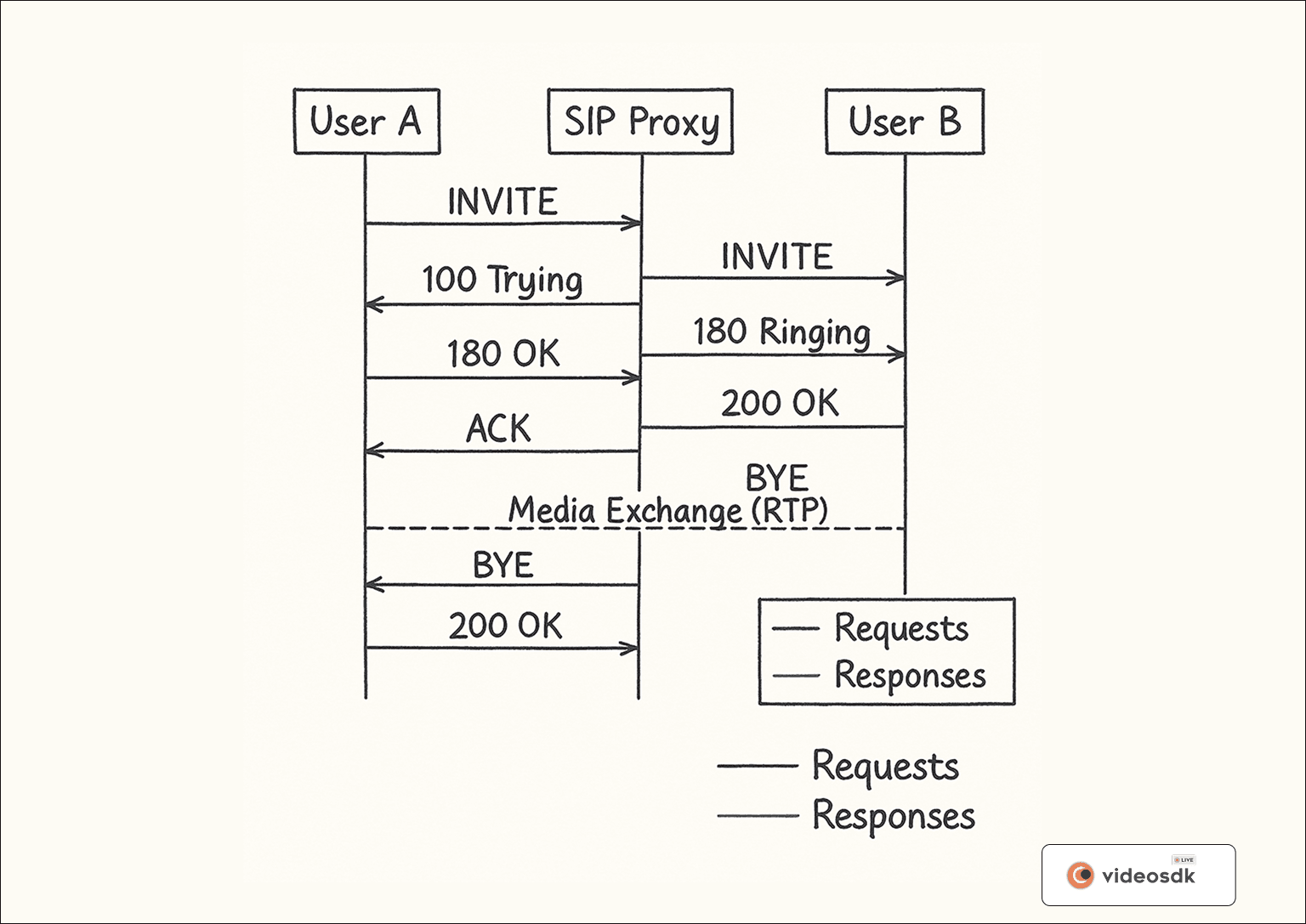
Figure 1: A comprehensive diagram of the SIP call flow showing the exchange of messages between User A, SIP Proxy, and User B. The diagram illustrates the complete lifecycle of a SIP call from initial INVITE to final BYE message, including all intermediate responses and the media exchange phase.
Key SIP Messages and Their Functions
SIP employs several message types, each serving distinct purposes in the communication process:
- INVITE: Initiates a session or changes parameters of an existing session
- ACK: Confirms reliable message exchanges
- BYE: Terminates a session
- CANCEL: Cancels a pending request
- REGISTER: Registers a user agent with a SIP server
- OPTIONS: Queries the capabilities of servers
- INFO: Sends mid-session information
- UPDATE: Modifies the state of a session without changing the state of the dialog
- REFER: Asks recipient to issue a request
- SUBSCRIBE: Requests notification of an event
- NOTIFY: Provides information about an event
SIP Proxies and Registrars: Key Components in Call Routing
The SIP architecture incorporates several server types that facilitate communication:
- Proxy Servers: Receive requests from clients and forward them to the next hop server. They can provide functions like authentication, authorization, network access control, routing, and security.
- Registrar Servers: Accept REGISTER requests and maintain a database of users and their current locations.
- Redirect Servers: Generate 3xx responses to requests, directing the client to contact an alternate set of URIs.
- Location Servers: Provide information about a caller's possible locations.
These components work together to ensure that SIP messages reach their intended recipients efficiently, even as users move between different networks and devices.
SIP Message Structure: A Closer Look
Header Fields: Understanding the Building Blocks
SIP messages consist of a start line, headers, and an optional message body. The headers contain crucial information for message processing and routing:
- To: Specifies the logical recipient of the request
- From: Indicates the logical identity of the request initiator
- Via: Records the SIP request route and is used to prevent message looping
- Call-ID: Uniquely identifies a specific invitation or all registrations of a particular client
- CSeq: Contains a sequence number and request method that increases for each new request
- Contact: Provides a URI for direct communication to a specific instance of the user agent
- Content-Type: Describes the message body format (e.g., application/sdp)
- Content-Length: Indicates the message body size in bytes
Here's an example of a typical SIP INVITE message header:
1INVITE sip:bob@example.com SIP/2.0
2Via: SIP/2.0/UDP pc33.example.com;branch=z9hG4bK776asdhds
3Max-Forwards: 70
4To: Bob <sip:bob@example.com>
5From: Alice <sip:alice@example.com>;tag=1928301774
6Call-ID: a84b4c76e66710@pc33.example.com
7CSeq: 314159 INVITE
8Contact: <sip:alice@pc33.example.com>
9Content-Type: application/sdp
10Content-Length: 142
11SDP (Session Description Protocol): Negotiating Media Capabilities
While SIP handles session establishment, the Session Description Protocol (SDP) defines the media parameters of the session. SDP is typically carried in the message body of SIP requests and responses, particularly INVITE and 200 OK messages.
SDP specifies:
- Media types (audio, video)
- Transport protocols (RTP/UDP/IP, etc.)
- Media formats (codecs)
- IP addresses and ports for media reception
- Timing information
- Other session attributes
Here's a simplified example of SDP content:
1v=0
2o=alice 2890844526 2890844526 IN IP4 pc33.example.com
3s=Session SDP
4c=IN IP4 pc33.example.com
5t=0 0
6m=audio 49172 RTP/AVP 0
7a=rtpmap:0 PCMU/8000
8m=video 51372 RTP/AVP 31
9a=rtpmap:31 H261/90000
10This SDP payload indicates that Alice is offering both audio (using G.711 μ-law codec) and video (using H.261 codec) streams.
SIP Stack Architecture: Deconstructing the Layers
User Agent Client (UAC) and User Agent Server (UAS)
At its core, the SIP protocol stack revolves around two fundamental components:
- User Agent Client (UAC): The client application that initiates SIP requests
- User Agent Server (UAS): The server application that responds to SIP requests
Interestingly, most SIP endpoints (phones, softphones) function as both UAC and UAS, initiating requests in some transactions and responding to requests in others. This dual nature allows for peer-to-peer communication while maintaining a client-server paradigm for individual transactions.
For example, when making a call, your phone acts as a UAC by sending an INVITE request. When receiving a call, it functions as a UAS by responding to an incoming INVITE.
Transport Protocols: UDP, TCP, and TLS
SIP's flexibility extends to its transport layer, where it can operate over several protocols:
- UDP (User Datagram Protocol): Offers fast, connectionless communication with minimal overhead. It's widely used for SIP but may face reliability issues with larger messages or in congested networks.
- TCP (Transmission Control Protocol): Provides reliable, connection-oriented communication. It ensures message delivery but with slightly higher latency and overhead.
- TLS (Transport Layer Security): Adds encryption to TCP connections, protecting SIP signaling from eavesdropping and tampering.
- SCTP (Stream Control Transmission Protocol): Less common but offers advantages like multi-homing and message-oriented operation.
The choice of transport protocol depends on specific requirements regarding reliability, security, and network conditions.
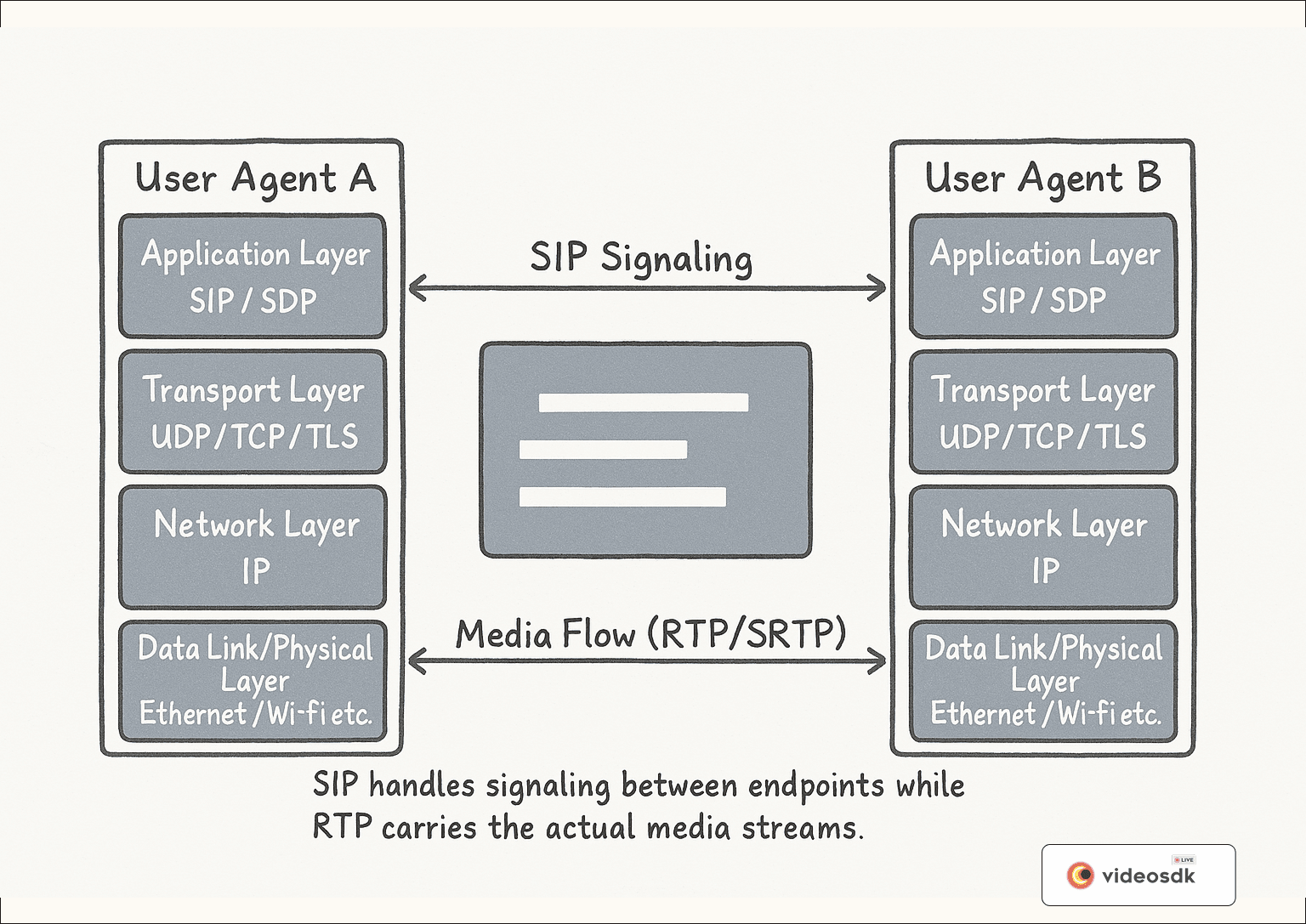
Figure 2: SIP Protocol Stack Architecture diagram showing the relationship between different protocol layers. The image illustrates how SIP operates at the application layer, while relying on transport protocols like UDP/TCP/TLS, and how media flows through RTP/SRTP separately from the signaling path. This layered structure shows the clear separation of concerns in the SIP architecture.
Real-Time Transport Protocol (RTP) and Secure RTP (SRTP)
While SIP handles signaling, the actual media (voice, video) travels via different protocols:
- RTP (Real-time Transport Protocol): Carries the media packets, providing payload type identification, sequence numbering, and timestamping.
- RTCP (RTP Control Protocol): Works alongside RTP to provide quality statistics and control information.
- SRTP (Secure RTP): Adds encryption, message authentication, and replay protection to RTP.
SIP and RTP work in tandem but independently – SIP establishes the session parameters (including which RTP ports to use), while RTP handles the continuous media transmission between endpoints once the session is established.
Practical Applications and Examples of SIP
SIP in VoIP Phones and Softphones
SIP has become the dominant protocol for IP telephony devices:
- Hardware IP Phones: Devices from manufacturers like Polycom, Cisco, and Grandstream use SIP to connect to VoIP services.
- Softphones: Software applications like X-Lite, Zoiper, and Bria implement SIP to turn computers and smartphones into VoIP endpoints.
- Mobile SIP Clients: Apps that allow smartphones to make VoIP calls over data networks rather than cellular voice networks.
Most business phone systems now use SIP as their primary communication protocol due to its flexibility and wide industry adoption. For any
web developer
building browser-based calling tools, VoIP dashboards, or real-time communication features, understanding how SIP works behind the scenes is essential for reliable implementation.SIP in Video Conferencing Systems
SIP's ability to handle multimedia sessions makes it ideal for video conferencing:
- Dedicated Video Conferencing Systems: Hardware from providers like Polycom and Cisco use SIP for call setup and management.
- Integrated Communications Platforms: Services like Microsoft Teams and Zoom leverage SIP (often alongside proprietary protocols) for certain types of connections.
- Interoperability Gateways: SIP helps bridge different video conferencing systems, allowing users on different platforms to communicate.
SIP Trunking: Connecting Businesses to the PSTN
SIP trunking
has transformed business telephony by replacing traditional PRI/T1 lines with internet-based connections:- Cost Savings: Eliminates the need for physical phone lines and reduces long-distance charges
- Scalability: Easily add or remove capacity without hardware changes
- Geographic Flexibility: Virtual numbers allow businesses to maintain presence in different regions
- Unified Communications: Integrates voice with other communication channels
Many telecommunications providers now offer
SIP trunking
services, allowing businesses to connect their IP PBX systems directly to the public switched telephone network (PSTN).The Future of SIP
WebRTC and its Impact on SIP
WebRTC
(Web Real-Time Communication) has emerged as a complementary technology to SIP:- Browser-Based Communication:
WebRTC
enables real-time communication directly in web browsers without plugins. - SIP Over WebSocket: This approach allows SIP to work within
WebRTC
environments, combining the strengths of both technologies. - Hybrid Approaches: Many modern communication platforms use both SIP and
WebRTC
, leveraging SIP for traditional telephony integration andWebRTC
for web-based clients.
Rather than replacing SIP,
WebRTC
has expanded the ecosystem, with each technology serving different aspects of the communication landscape.Security Considerations and Enhancements
As communications move to IP networks, security becomes increasingly important:
- SIP over TLS: Encrypts signaling to prevent eavesdropping and man-in-the-middle attacks
- SRTP: Protects media streams from interception
- Identity Management: Improvements in authentication and authorization mechanisms
- Fraud Prevention: Enhanced methods to prevent toll fraud and service theft
- STIR/SHAKEN: Frameworks for combating caller ID spoofing and robocalls
The evolution of SIP security continues to address emerging threats while maintaining compatibility with existing systems.
Key Takeaways
- SIP is an application-layer protocol that establishes, modifies, and terminates multimedia sessions.
- The SIP call flow follows a logical sequence involving INVITE, response codes, and acknowledgments.
- SIP messages contain headers with routing and identification information, while SDP in the message body negotiates media capabilities.
- The SIP stack architecture includes UAC and UAS components and can operate over various transport protocols.
- SIP powers VoIP phones, video conferencing, and
SIP trunking
services in practical applications. - Security enhancements and integration with technologies like
WebRTC
represent the future direction of SIP.
Conclusion
The Session Initiation Protocol represents a cornerstone of modern communication infrastructure, enabling the voice and video services we rely on daily. By understanding SIP's fundamental principles—from its message structure to its call flow and architectural components—developers and IT professionals can better implement, troubleshoot, and optimize communication systems.
As digital transformation continues to reshape businesses and personal communications, SIP's role will likely evolve but remain essential. Whether you're developing a new VoIP application, managing an enterprise phone system, or simply curious about how your internet calls work, a solid grasp of SIP provides valuable insight into the technologies connecting our digital world.
Want to level-up your learning? Subscribe now
Subscribe to our newsletter for more tech based insights
FAQ